
Ahmyth logo from the Github page
I made a video recently where I talked about how to hack an Android device with msfvevnom and Kali Linux. In this post we will use Ahmyth, a tool which is going to create an apk that will be used on a target device to gain remote control.
I will cover the Windows 10 version, keep also in mind that this tool is not going to work on every Android version.
Tools to use and other requirements
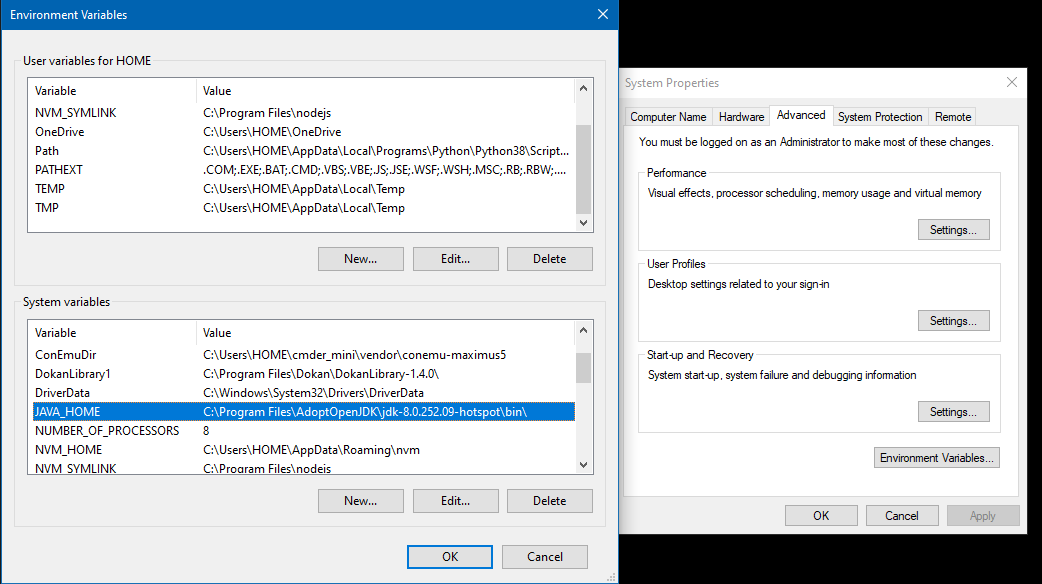
To use this tool you just need Java 8 which can be downloaded with the Open JDK. If you already have another Java version installed, you should check in the environment variables of Windows 10, if JAVA_HOME is set correctly. In my case it is the following:
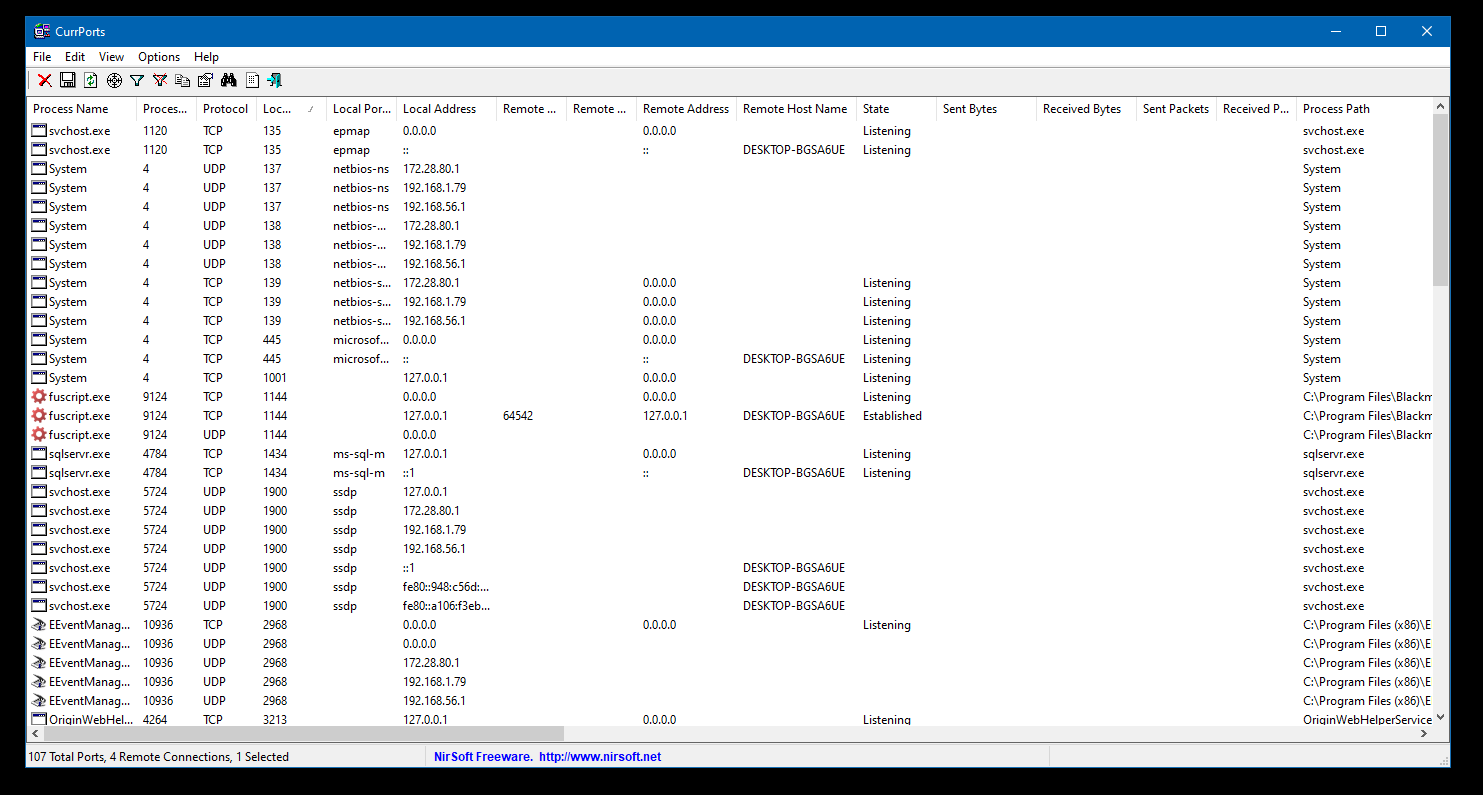
CurrPorts is not required but it will show you if the default port 42474 is not already used by another process. It simply displays the list of all currently opened TCP/IP and UDP ports on your local computer. For example:
Remember to disable the antivirus or to add an exclusion to the file created by Ahmyth, otherwise Windows Defender will simply remove it.
Here you can find the necessary links to download the tools:
Let’s set up everything
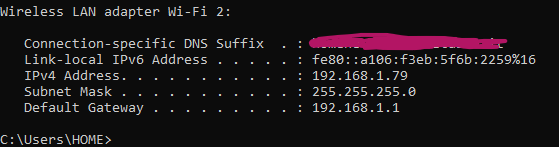
It should be obvious but in order to get your IP address on Windows, open the comand prompt, type “ipconfig” and check the value IPV4 Address:
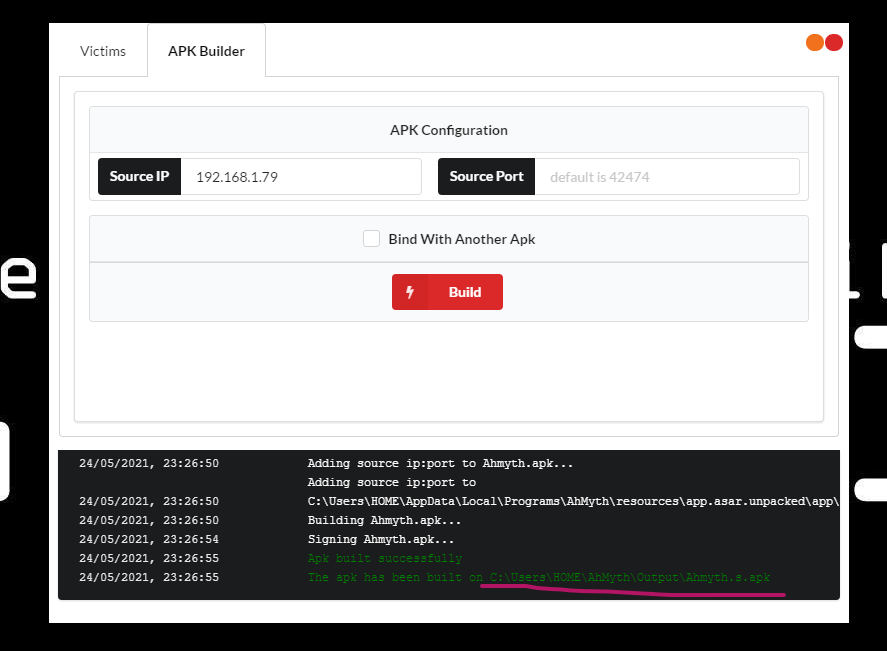
Open Ahmyth and click on APK Builder on the top of the window, set your IP in Source IP and press Build, if everything is correct you should get an output highlighted in green like this:
Now we need to download the apk on the target device, I’m using Bluestacks as emulator but you can use something else. We could just import the file into our emulator, but it would be better to download the file through a server. On Linux you need apache2 to create a server, then we can copy our apk into the following path /var/www/html.
On your Linux terminal type these commands depending where you copied the apk:
- To move the file type
$ sudo mv Ahmyth.s.apk /var/www/html
- Check if apache2 is not already active
$ service apache2 status
- Start apache2 if it is not running
$ sudo service apache2 start
- Check the IP Address of the Linux VM, you will use it later
$ ifconfig
Install the apk on the target device
Next thing that we need to do is to download the apk on the target device, let’s open the browser in the emulator by typing the IP found in the Linux VM and the file that we moved into the path "/var/www/html". For example:
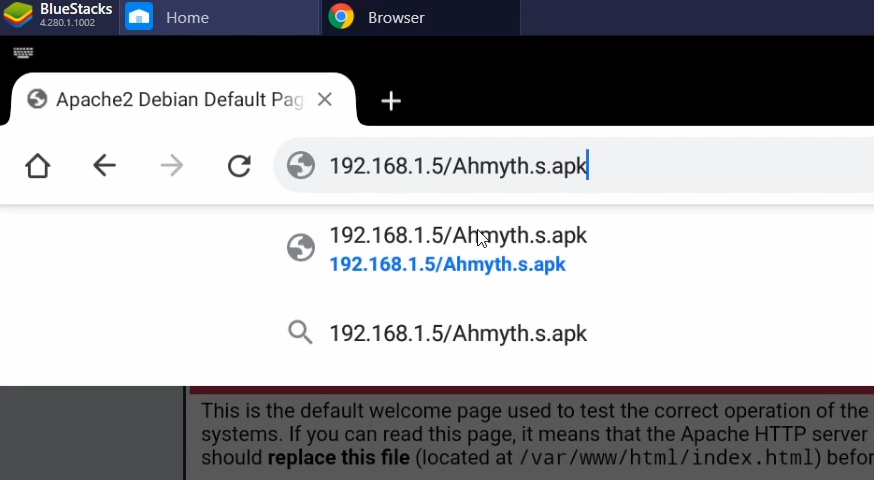
Before we install the apk we have to set up a listener with Ahmyth, go to the Victims tab and click on Listen, you should get a console output higlighted again in green:
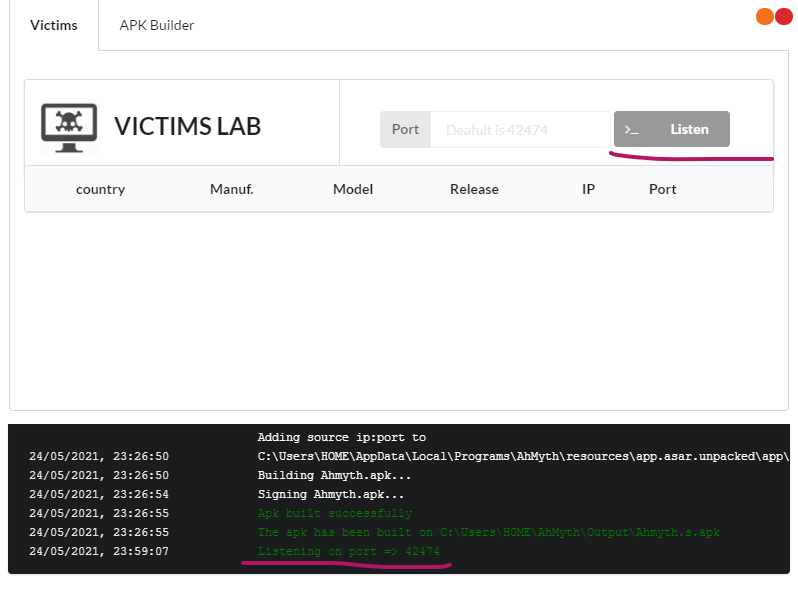
If everything is correct, you should be able to connect to the victim, let’s see it in action:
TLDR
This was a simple demonstration to exploit an Android device with a tool like Ahmyth, of course this tool is not the best choice because it will be detected by the antivirus very easily and many Android versions are not working with this tool. However some of these features can be cloned in Metasploit to get the same result, it is more complex but who doesn’t love the complex challenges ? And remember, be ethical!